
Hacker group Anonymous have published a guide for people interested in waging an online war against ISIS.
The guide will detail ways to identify and attack websites and social media assets belonging to the Islamic State or ISIS.
International Business Times reports:

BYPASS THE CENSORS
Sign up to get unfiltered news delivered straight to your inbox.
You can unsubscribe any time. By subscribing you agree to our Terms of Use
In the wake of the terror attacks in Paris on Friday, Anonymous vowed to hunt down those responsible and expose them, calling Operation Paris (or OpParis) “the biggest operation ever” against the extremist group. Earlier this year, an offshoot of Anonymous called GhostSec began tracking Twitter accounts associated with ISIS in an attempt to weaken their ability to spread their propaganda online.
In the days since OpParis began, various groups within Anonymous have claimed to have identified tens of thousands of Twitter accounts and taken them offline, as well as targeting some ISIS-related websites, including one that it claims was a recruitment site for the terrorists, which is now permanently offline. According to the official Twitter account for the campaign, the group’s next plan is to spam ISIS-related Twitter hashtags — and it is currently running a poll to find out whether to rickroll the accounts or spam them with a “pool is closed image.” So far, rickrolling has the edge:
What to spam IS hastags with…
— #OpParis (@opparisofficial) November 18, 2015
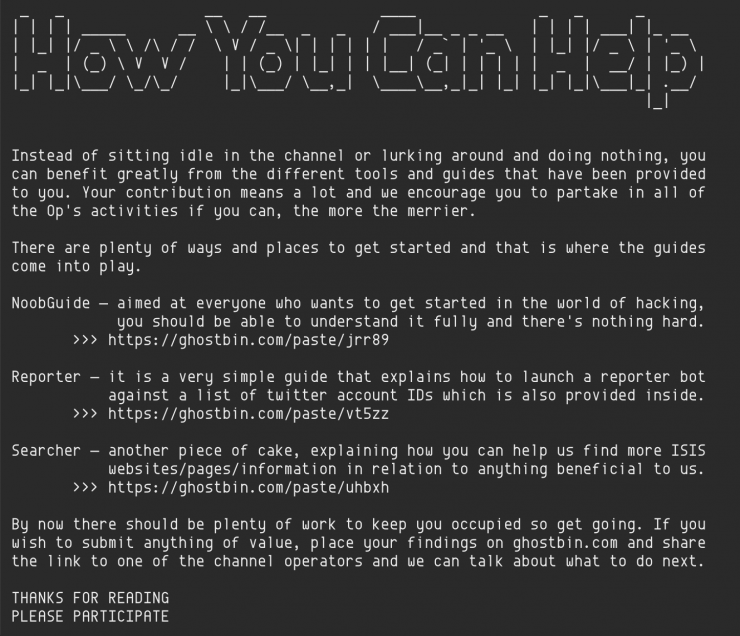
The Noob Guide
The group is currently collecting Twitter account details from its followers before verifying them “by trusted individuals” and then passing them onto the authorities for surveillance. To help this effort the group has created a trio of guides, with the first, dubbed “The Noob Guide” being aimed “at everyone who wants to get started in the world of hacking” and promising that the instructions are easy to understand.
“Your contribution means a lot and we encourage you to partake in all of the Op’s activities if you can, the more the merrier,” the group says.
The guide itself first gives some tips for newbies, including learning some HTML and even some Python programming language, before starting out. It then suggests you use the Linux operating system recommending three flavors (or distributions) of Linux to use. The guide then speaks about protecting your anonymity, including the user of the Tor browser and virtual private machines (VPNs).
Next, the group gives users a list of hacking tools that they can use without needing in-depth coding or computer knowledge. These include tools for carrying out distributed denial of service (DDoS) attacks, cracking passwords, scanning websites for vulnerabilities and man-in-the-middle attacks.
Read More: ibtimes.com/how-hack-isis-anonymous-publishes-guide-help-attack-islamic-states-online-presence
Edmondo Burr
CEO
Assistant Editor
Latest posts by Edmondo Burr (see all)
- Police Arrest Suspect In Supermarket Baby Food Poisoning - October 1, 2017
- Seoul Secures Data From Electromagnetic Interference By N Korea - September 30, 2017
- The ‘World’s First Internet War’ Has Begun: Julian Assange - September 30, 2017


Anonymous has no leaders.
Anonymous is not organized by anyone.
Anonymous can be anything, or it can be nothing at all.
Anonymous isn’t simply a group of internet hackers.
Anonymous has no form.
Anonymous is everyone, yet it can be no-one.
Anonymous does nothing for recognition.
Anonymous is a concept, not a group. Don’t forget that.
We are Anonymous. We are united by one, divided by none.
We are Legion. We do not forgive. We do not forget. Expect us.
Anonymous has no leaders.
Anonymous is not organized by anyone.
Anonymous can be anything, or it can be nothing at all.
Anonymous isn’t simply a group of internet hackers.
Anonymous has no form.
Anonymous is everyone, yet it can be no-one.
Anonymous does nothing for recognition.
Anonymous is a concept, not a group. Don’t forget that.
We are Anonymous. We are united by one, divided by none.
We are Legion. We do not forgive. We do not forget. Expect us.