The US National Security Agency (NSA) has figured out how to hide spying software deep within hard drives giving the agency the means to eavesdrop on the majority of the world’s computers, according to cyber researchers and former operatives. The software allows them to monitor computers, even when they are not connected to the internet.
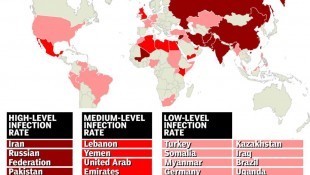
Kaspersky Lab, A Moscow-based security software maker, that has exposed a series of Western cyber-espionage operations, said it had found personal computers in 30 countries infected with one or more of the spying programs.

BYPASS THE CENSORS
Sign up to get unfiltered news delivered straight to your inbox.
You can unsubscribe any time. By subscribing you agree to our Terms of Use
Latest Video
Most of the most infections were seen in Iran, followed by Russia, Pakistan, Afghanistan, China, Mali, Syria, Yemen and Algeria.
The Mail Online reports: The targets included government and military institutions, telecommunication companies, banks, energy companies, nuclear researchers, media, and Islamic activists.
The NSA began infecting computers in 2001 claims Kaspersky, ramping up their efforts in 2008 when President Barack Obama was elected.
This ‘surpasses anything known in terms of complexity and sophistication of techniques, and that has been active for almost two decades,’ said Kaspersky.
What’s more, even the makers of these hard drives are unaware that these spying programs have been installed, with the NSA obtaining their source codes by going so far as to pose as software developers according to former intelligence operatives, or telling the companies the government must do a security audit to make sure their source code is safe.
According to Kaspersky, the spies made a technological breakthrough by figuring out how to lodge malicious software in the obscure code called firmware that launches every time a computer is turned on.
Disk drive firmware is viewed by spies and cybersecurity experts as the second-most valuable real estate on a PC for a hacker, second only to the BIOS code invoked automatically as a computer boots up.
‘The hardware will be able to infect the computer over and over,’ lead Kaspersky researcher Costin Raiu said in an interview.
Though the leaders of the still-active espionage campaign could have taken control of thousands of PCs, giving them the ability to steal files or eavesdrop on anything they wanted, the spies were selective and only established full remote control over machines belonging to the most desirable foreign targets, according to Raiu. He said Kaspersky found only a few especially high-value computers with the hard-drive infections.
The firm declined to publicly name the country behind the spying campaign, but said it was closely linked to Stuxnet, the NSA-led cyberweapon that was used to attack Iran’s uranium enrichment facility. The NSA is the U.S. agency responsible for gathering electronic intelligence.
A former NSA employee told Reuters that Kaspersky’s analysis was correct, and that people still in the spy agency valued these espionage programs as highly as Stuxnet. Another former intelligence operative confirmed that the NSA had developed the prized technique of concealing spyware in hard drives, but said he did not know which spy efforts relied on it.
NSA spokeswoman Vanee Vines said the agency was aware of the Kaspersky report but would not comment on it publicly.