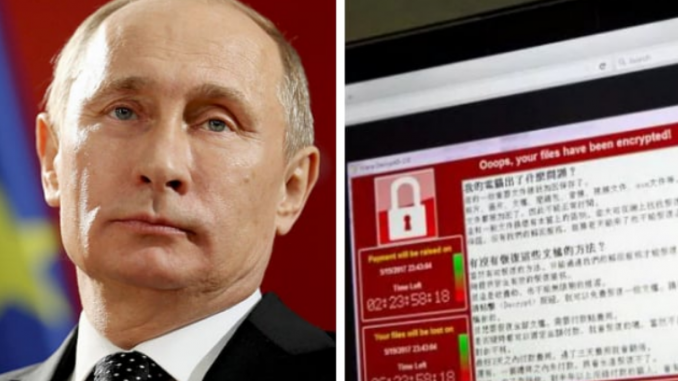
A massive European cyberattack currently being blamed on Russian President Vladimir Putin, actually originated from the CIA according to WikiLeaks documents.
The attack, nicknamed Petya, used a ransomware worm to target corporations across the globe, including banks and airports in the Ukraine, causing chaos around the world.

BYPASS THE CENSORS
Sign up to get unfiltered news delivered straight to your inbox.
You can unsubscribe any time. By subscribing you agree to our Terms of Use
Latest Video
NATO chief Jens Stoltenberg has vowed to trigger the Article 5 mutual defence commitment, punishing Russia for the attacks and moving the world one stage closer to World War 3.
“We exercise more, we share best practices and technology and we also work more and more closely with all allies,” Stoltenberg told reporters ahead of a NATO defence ministers meeting in Brussels on Thursday.
However, Wikileaks Vault 7 documents reveal that the attacks were likely a false flag operation by the CIA using their UMBRAGE hacking tools, designed to frame Russia and create a global conflict.
Businessinsider.com reports: Analysts at several cybersecurity firms have confirmed that the Petya assault used a powerful and dangerous cyberweapon created by the US National Security Agency that was leaked in April by the hacker group Shadow Brokers.
Symantec analysts have confirmed #Petya #ransomware, like #WannaCry, is using #EternalBlue exploit to spread
— Threat Intelligence (@threatintel) June 27, 2017
Though it’s too soon to be certain, experts say it seems as though a confluence of factors may be pointing to Russian state involvement in carrying out the attack.
‘Ukraine was targeted’
Ukraine was hardest hit by the attack, which came one day before the country’s Constitution Day.
Russia and Ukraine’s rocky relationship has been well-documented, and it has seen a steep decline since Russia annexed the territory of Crimea in 2014 and steadily pursued greater military aggression toward its neighbor.
“The first thing that raises a red flag to me is that, right now, Ukraine’s main antagonist is Russia,” said Alex McGeorge, the head of threat intelligence at Immunity Inc., a cybersecurity firm that specializes in nation-state cyberthreats.
McGeorge added that the methodology of the attack also “gives a really good and stable foothold on networks that would matter to somebody who was interested in attacking Ukraine.”
“If I’m interested in disrupting Ukraine, this is great for me,” he said.
In addition to major disturbances to the Ukrainian power grid, banks, government offices, and airports, the country was forced to manually perform radiation checks at the site of the contaminated Chernobyl nuclear power plant after its operations were disrupted.
Anton Gerashchenko, an adviser to Ukraine’s interior minister, wrote in a Facebook post that the attack was “the largest in the history of Ukraine.”
Greg Martin, the CEO of the cybersecurity firm JASK, said he thought that because of its political climate and the geopolitical factors at play, “Ukraine was targeted by bad actors who have been using it as a cyberweapon testing ground over the past couple of years.”
In 2015, a massive cyberattack leveled against the country’s power grid cut electricity to almost 250,000 Ukrainians. Cybersecurity experts linked the attack to IP addresses associated with Russia. Since then, Wired magazine’s Andy Greenberg reported last week, Ukraine has seen a growing crisis in which an increasing number of Ukrainian corporations and government agencies have been hit by cyberattacks in a “rapid, remorseless succession.”
Ukraine is now host to what may turn into a full-blown cyberwar, Greenberg reported. Two separate attacks on the country’s power grid were part of what Greenberg called a “digital blitzkrieg” waged against it for the past three years, which multiple analysts have connected to Russian interests.
“You can’t really find a space in Ukraine where there hasn’t been an attack,” Kenneth Geers, a NATO ambassador focusing on cybersecurity, told Wired.
“What we know about the Russians is that it’s part of their M.O. and they sow chaos wherever they can,” McGeorge said. “Having this foothold everywhere for all these important Ukrainian networks speaks directly to that goal.”
‘The numbers just don’t work’
Ransomware attacks typically lock users out of their computer systems until they pay a ransom.
Analysts, however, have cast doubt on the notion that Tuesday’s attack was carried out in an attempt to make money, because it’s unlikely that the actor or actors behind it will recoup any investment from their efforts.
The hackers behind a crippling cyberattack carried out in May, dubbed WannaCry, made about $50,000 worth of the bitcoin cryptocurrency.
“The numbers just don’t work,” McGeorge said. WannaCry’s accumulation, he said, was “a pittance when you’re talking about nation-state levels.”
And it’s likely that Tuesday’s attack will yield even less than that.
The attack was carried out using an email address that was taken down within the first day of the infection occurring. That, McGeorge said, proved “there was never a chance that someone was going to be able to cash in on this.”
“If you’re doing a massive ransomware campaign,” he said, “you have to have resiliency built into the way you get paid. We don’t see a lot of that here.”
“Traditionally, the ransomware attack has not been the tool of a nation-state,” said Jason Glassberg, the cofounder of Casaba Security. But maintaining the appearance of a ransomware attack could lend a nation-state the cover of plausible deniability, he added.
“The ransomware aspect to this could actually provide Russia with a great point of distraction to control the narrative when discussing the attack,” McGeorge said.
Russian companies said they were struck, but most quickly recovered
In addition to several other companies, Russia’s state-owned oil company, Rosneft, also reported that it was attacked, as did the Russian steelmaker Evraz.
While the attack brought serious consequences for other corporations — like the shipping giant Maersk — neither Rosneft nor Evraz suffered similar fallout. Rosneft said its oil production had not been affected, and Evraz said the attack had not affected its output.
Ukraine relies heavily on Russia for its oil and natural-gas reserves, and it’s likely that Rosneft was hit by the attack because it regularly deals with the Ukrainian government.
“But one of the standing gentleman’s agreements the FSB,” the Russian intelligence agency, “has with the Russian hacking community is, ‘Do whatever you want, so long as it doesn’t hurt Russia,'” McGeorge said.
And while hackers can’t stop these companies from getting infected, they can stop the attack from propagating, which is most likely why neither Rosneft nor Evraz saw significant damage to its output, McGeorge added.
Home Credit Bank, one of Russia’s top 50 lenders, however, saw significant disruption in its operations. The bank was reportedly paralyzed and was forced to shut down all its offices on Tuesday.
Tuesday’s attack was the second serious cyberattack carried out in a little over a month. Though it’s still too early to drawn any conclusions, if this attack has Russian origins, Martin of JASK said, “we can expect that it will be much more far-reaching and sophisticated.”
“But it still might just be a harbinger of what’s to come in the future,” Glassberg said.


