
Researchers have discovered a way in which hackers could potentially track a user’s keystrokes simply by monitoring WiFi signals.
According to researchers from Michigan State University and Nanjing University in China, the “WiKey” system allows hackers to exploit WiFi devices (including routers) due to their multiple-input and multiple-output (MIMO) capabilities.
Bleepingcomputer.com reports:

BYPASS THE CENSORS
Sign up to get unfiltered news delivered straight to your inbox.
You can unsubscribe any time. By subscribing you agree to our Terms of Use
“Each MIMO channel between each transmit-receive (TX-RX) antenna pair of a transmitter and receiver comprises of multiple sub-carriers. These WiFi devices continuously monitor the state of the wireless channel to effectively perform transmit power allocations and rate adaptations for each individual MIMOstream such that the available capacity of the wireless channel is maximally utilized….”
In other words, most routers have the ability to monitor a wireless channel’s behavior and pick up on its channel state information (CSI). Those CSI values, in turn, characterize something that’s known as Channel Frequency Response (CFR), or fluctuations in signal exhibited between each antenna pair for a subcarrier.
Those fluctuations reveal a lot about a WiFi channel. As it turns out, they can even reveal hand and finger movements–that is, a user’s keystrokes.
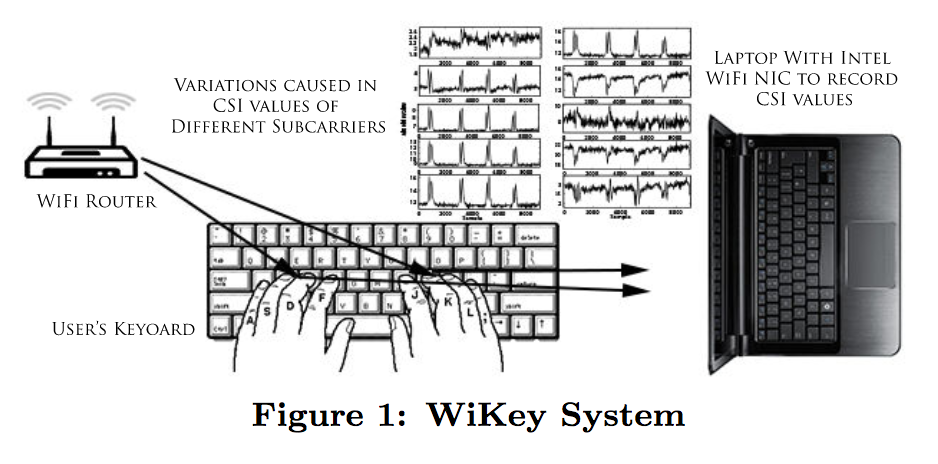
In their experiment, the researchers used a TP-Link TL-WR1043ND WiFi router and a Lenovo X200 laptop. While a subject typed on the laptop, the researcher used the router’s antennas to pick up all existing CSI values. They then passed that data through several different types of filtering to eliminate other sources of noise and to isolate the keystrokes.
Using a specially designed algorithm, the researchers were able to identify that each keystroke had a start- and endpoint and that it rose and fell like a wave. This information proved instrumental in extracting the actual keystrokes themselves.
Overall, WiKey registered a 96.4 percent success rate in classifying single keystrokes. That accuracy fell slightly to 93.5 percent when researchers adjusted the experiment so that the subject typed keys in a continuous sentence.
Computer criminals and researchers have looking at keyboard security for years now. Through their combined efforts, they’ve not only demonstrated that malware can intercept keystrokes in the form of FM radio signals from an isolated computer; they’ve also proven that a user can be identified and tracked based upon how they type. Clearly, WiKey builds upon that existing body of research.
That’s not to say the system is without limitations. For the experiment, researchers set a number of controls, such as an environment with very little noise, a close device proximity of two meters between the router and the keyboard, and training requirements that spanned only over the course of one day and which required the subjects to not move their heads or other parts of their body. In the real world, everything is a lot more dynamic.
The researchers know that, and they’re hoping to improve on their system so that it accounts for such factors:
“…[I]n future we plan to address the problem of mitigating the effects of more harsh wireless en-vironments by building on our micro-gesture extraction and recognition techniques proposed in this paper.”
For more information about WiKey, check out the researchers’ paper here.


